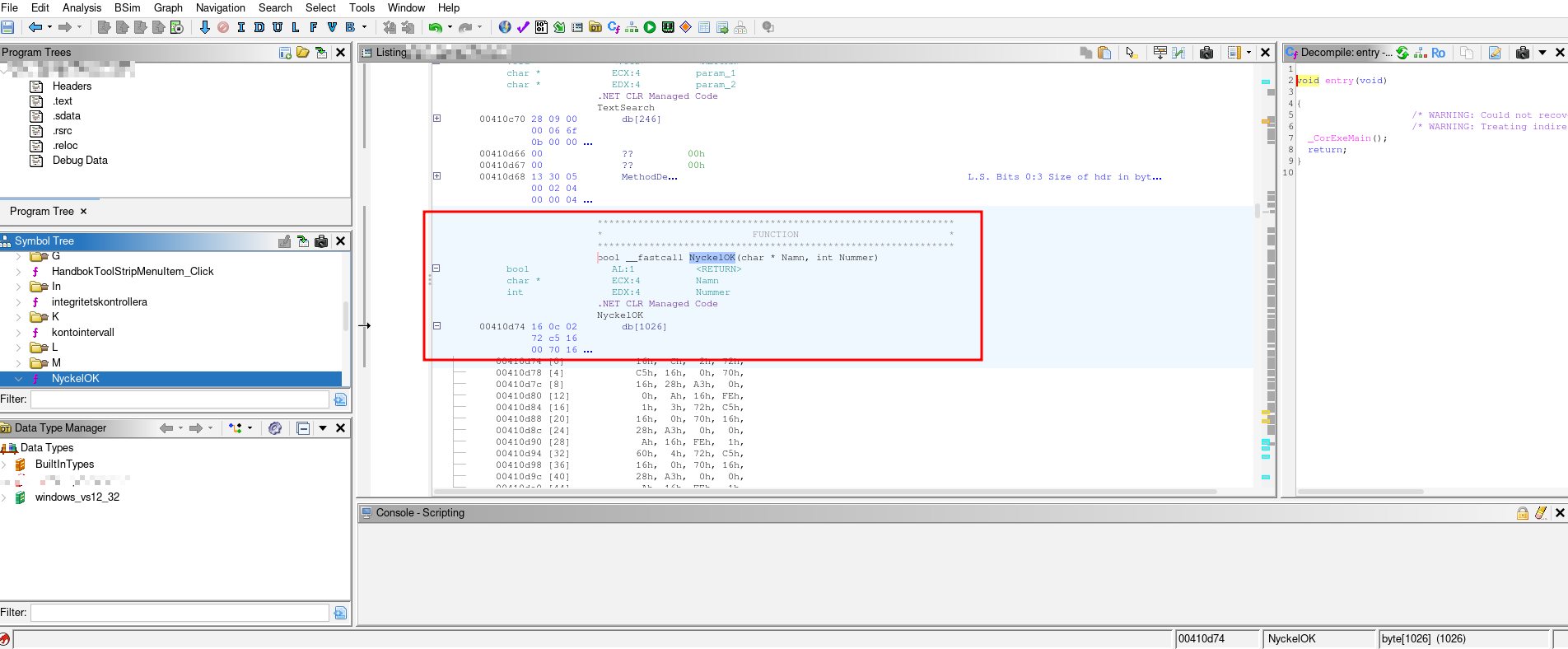
Reverse engineer a serial key validator A bit of nostalgia As many kids in my generation, I grew up with video games and the big question was always "Who is gonna be the host for the LAN party this weekend?". Same question. Every. Single. Weekend.
This was in late 90s, and we were about 10-12 years old, so we did not have a lot of money. We were lucky to have network equipment (mostly cables, switches, hubs.