Reverse engineer a serial key validator
A bit of nostalgia
As many kids in my generation, I grew up with video games and the big question was always "Who is gonna be the host for the LAN party this weekend?". Same question. Every. Single. Weekend.
This was in late 90s, and we were about 10-12 years old, so we did not have a lot of money. We were lucky to have network equipment (mostly cables, switches, hubs..) sponsored by companies or family members, which were great.
But we didn't have a lot of money to buy games. We had to share them, and the only way to do that was to copy the game from one computer to another. But most games had a serial key that you had to enter during installation, and you couldn't just copy the game files, you also needed the serial key, or somehow bypass the serial key check.
To be honest, my biggest passion was never to play those games. I enjoyed the athmosphere of the LAN party, the social aspect, the fun of playing together with friends every now and then. But I was mostly working with my own programming projects in the middle of gunfire between Terrorists and Counter-terrorists or a massive slaughter of Zerglings.
Writing cracks, serial key generators or trainers to various games was never my life goal, but it was a fun challenge and, above all, it was something that was needed and appreciated.
The tools I had at my disposal was a simple hex editor and the instruction set referance manuals for the x86 architecture. I found all memory locations, decoded the hex values by hand. It was a tedious work. Then I modified the game files to either bypass the serial key check, or CD-ROM check or whatever I wanted to bypass.
It was a fun time.
Today
I started to use Linux and Open Source software short after that, and I haven't wrote a crack nor serial key generator since then.
I still reverse engineer stuff every now and then, both in my profession and for fun. Mostly to get root access to devices that I own but don't have the source code for.
To that I've used IDA [1], but now mostly Ghidra [2], which are both great tools for reverse engineering.
The !challenge
Today I came across a software that needed a serial key for activation. I do not have any interrest in the software itself and I'm not planning to use it nor spoil which software it is. But create a serial key generator for it in the meantime I waited for my Yocto build to finish sounded like a fun challenge. It turns out not to be a challenge at all, in fact, my Yocto build was not even finished when I had the serial key generator ready.
Ghidra
First I analysed the code in Ghidra. I found a function that looked like it was doing the serial key check, but it was .NET CLR Managed Code, unfortunately, Ghidra does not support that.
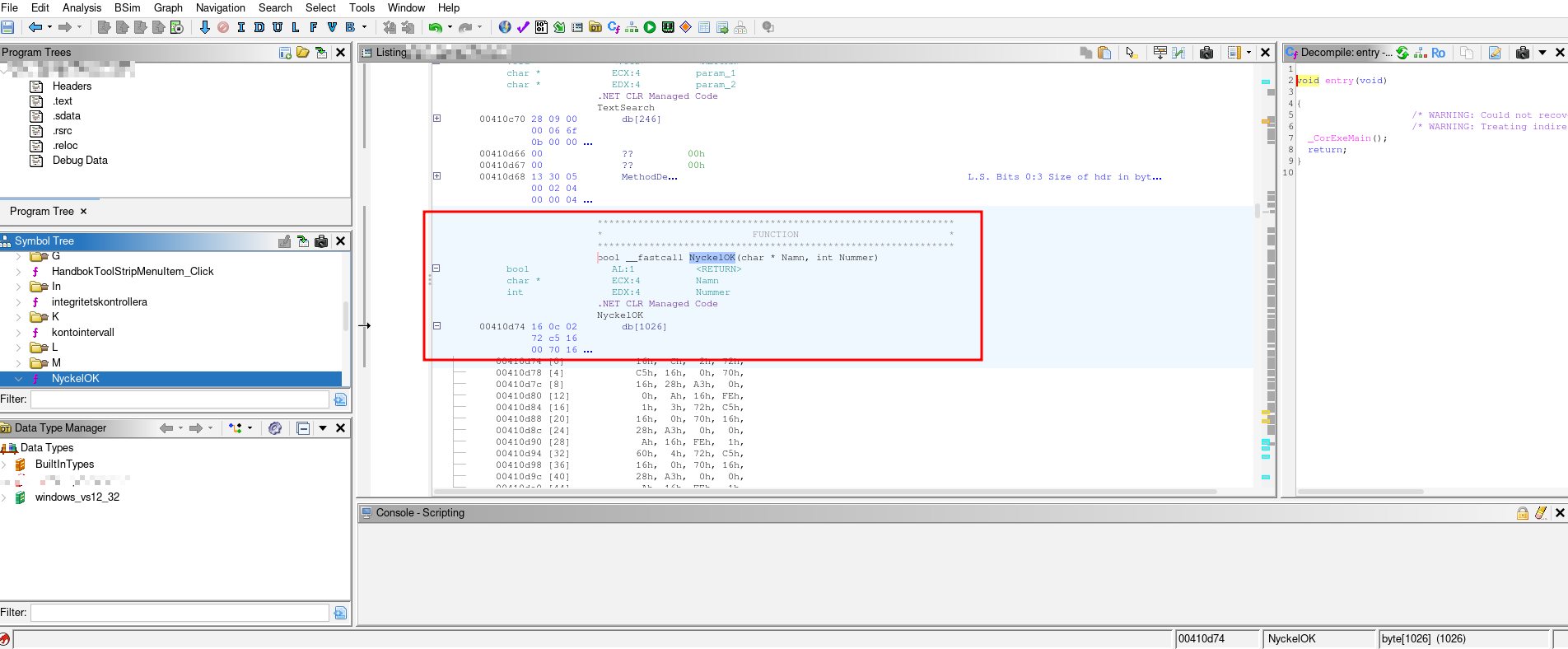
VSCode and ILSPY
I downloaded VSCode and ILSPY [3] to decompile the .NET code. Looked up the symbol I found previously and... there it was. Everything is in clear text, no obfuscation, no protection, no anti-debugging, no anti-tampering, nothing.
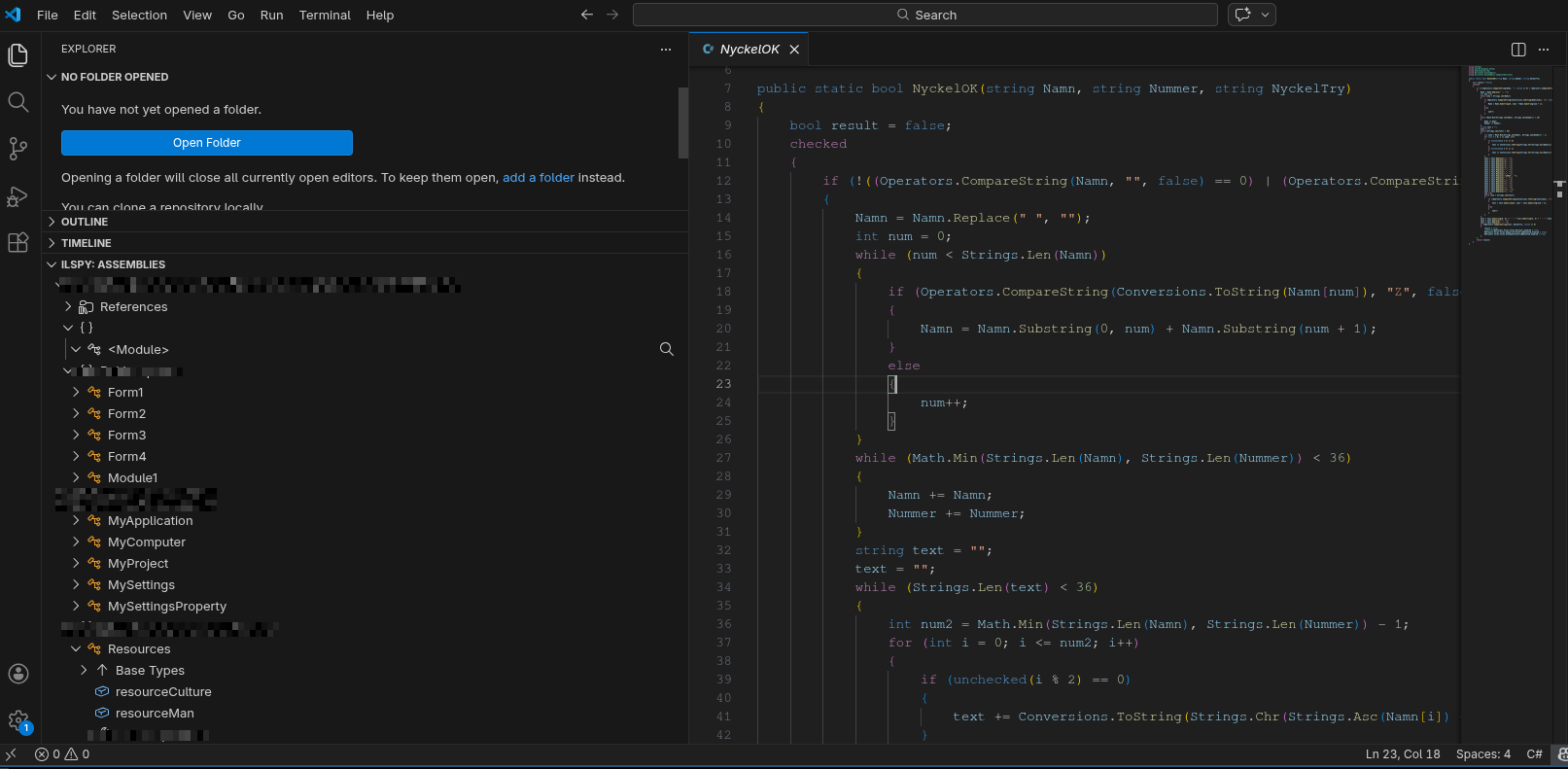
Rewrite to C++
I rewrote the the code to C++ and compiled it.

It worked.
Final thoughs
The application is written by a small company, it is not overpriced and it does what it is supposed to do.
I'm aware of that copy protection isn't the main focus for this company, and I don't think they have spent many hours on it and that's fine. Even if it is a 10-minute hack to bypass, it still provides some level of protection and that is good enough in many cases.
So, what is the point of this blog post? I don't know, maybe it's just a fun story about how I reverse engineered a serial key validator in 10 minutes, or maybe it's a reminder that copy protection is more about providing some level of protection rather than being unbreakable, and that is fine.